4G Security: Hacking USB Modem and SIM Card via SMSThe vulnerability4G modemSIM Card vulnerabilityVideo
The research team which comprised of Sergey Gordeychik, Alexander Zaitsev, Kirill Nesterov, Alexey Osipov, Timur Yunusov, Dmitry Sklyarov, Gleb Gritsai, Dmitry Kurbatov, Sergey Puzankov and Pavel Novikov, presented briefing about the above vulnerabilities at the recently concluded Choas Computer Club hackers conference in Hamburg, Germany as well as at the PacSec Conference held at Tokyo.
The vulnerability
Researchers from Positive Technologies made a detailed briefing about how detailing how to compromise 4G USB modems and how the SIM cards are vulnerable to exploitation via SMS over 4G networks.
4G modem
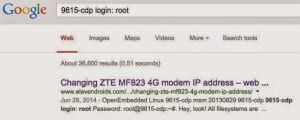
The Positive Technology researchers used six USB modems with 20 separate firmware installations to test their vulnerabilities and found that out of these, only three firmware installations could resist the attack. The researches found the passwords for Telnet access on Google Search and used http access to monitor the communications.
After connecting their USB modems to their machines and listing the devices as distinct nodes with web applications, the researchers were able to launch browser-based cross-site request (CSRF) forgery, cross-site scripting (XSS) and remote code execution (RCE) attacks.
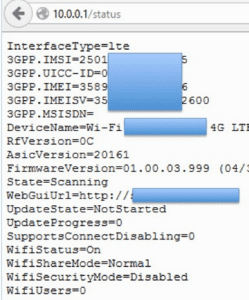
Once hacked, the researchers managed to obtain confidential information regarding international mobile subscriber identities (IMSI), universal integrated circuit cards (UICC), international mobile station equipment identities (IMEI) and software versions, device names, firmware versions, WI-Fi statuses and more.
In addition to information, the researchers found out that they can compel the modem to to the following without any interference :
change DNS settings (to sniff traffic), change SMS center settings (to intercept and interfere with SMS), change the password on the self-service portal by sending an SMS (to transfer money by subscribing to a third-party service), lock the modem by deliberately entering wrong PIN or PUK codes, remotely “update” the modem’s firmware to a vulnerable version.
The researchers said that the vulnerability can be further exploited to access the computer. In this regard, the researchers from Positive Technology blog state,
SIM Card vulnerability
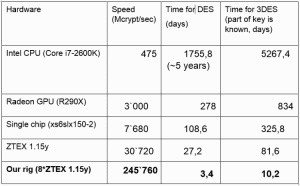
SIM cards are vulnerable as per the researchers the numbers is considerably less. The researchers managed to exploit only 20 of the 100 SIM cards they obtained for testing. By sending a binary SMS, the researchers managed to lock SIM cards and sniff and decrypt device traffic. “One way to do it is to install a USB keyboard driver, which causes the computer to identify the modem as an input device. Use this pseudo keyboard to issue the command to reboot the system from an external disk, aka the very same modem.” They added, “Then all that is left to do is to install a bootkit that allows you to remotely control the device.” The researchers stated that they tested the SIM cards to check whether they could brute-force the data encryption standard (DES) keys protecting the SIM, which they did. However breaking the 3DES encryption keys took a tad longer for the researchers. “To brute-force DES keys, we use a set of field-programmable gate arrays (FPGA), which became trendy for Bitcoin mining a couple of years ago and got cheaper after the hype was over.” They added that, “The speed of our 8 modules *ZTEX 1.15y board with the price tag of 2,000 Euro is 245.760 Mcrypt/sec. It is enough to obtain the key within 3 days.”
It took them 10 days with the fastest speed to break the 3DES key and 3 to 4 days to break the DES keys. In normal circumstance, a home computer with Intel Core i7-2600k CPU would take roughly five years to break DES and more than 20 years to break 3DES, they said. Once DES or 3DES key is broken, researchers said they could issue commands to toolkit applications (TAR). One such TAR is a file system that stores TMSI (Temporary Mobile Subscriber Identity) and Kc (Ciphering Key). Once hacked, a potential hacker can perform the following actions via a binary SMS:
decrypt subscriber traffic without using brute force attacks on DES, spoof a subscriber’s identity (receive his/her calls and SMS), track a subscriber’s whereabouts, cause DOS by entering 3 wrong PIN codes and 10 wrong PUK codes in a row if PIN code is enabled for file system protection.
The research have stated that mobile telephone is not limited to smartphone users as more and more products and critical infrastructure installations like Industrial Control System (ICS) and Supervisory Control And Data Acquisition (SCADA) machines use mobile communication technology which is partly or based largely on GSM standard. Certain ATMs also deploy these USB modem technologies to remotely transmit payment data. Considering the risks involved, the researchers have brought forward vulnerabilities which should be addressed as soon as possible by the stake holders.
Video
The video of the presentation they made is given below Resource : Positive Technologies Blog.