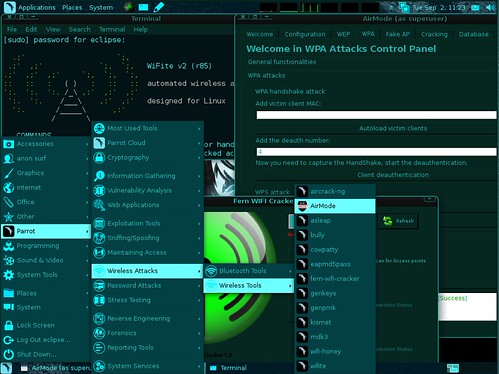
Parrot Security OS for Pentesting, Computer Forensic, Reverse engineering, Hacking, Cloud pentesting, Privacy/Anonimity and CryptographyFeatures
According to its developers, Parrot Security OS is a security oriented operating system designed for Penetration Testing, Computer Forensic, Reverse engineering, Hacking, Privacy/Anonymity and Cryptography.
Instead of installing the OS then painstakingly assembling your collection of security tools (and package dependencies), using something like Parrot Security OS takes care of all that for you It is based on Debian and developed by Frozenbox network. Parrot is designed for everyone, from the Pro pen-tester to the newbie, because it provides the most professional tools combined in a easy to use, fast and lightweight pen-testing environment, and it can be used also for an everyday use. Most of the penetration testing tools can be found under the Parrot entry of the main menu, where they’re organized in subsections. In addition, an anonymous surfing mode is available for those who don’t want to be traced. Among the included applications, we can mention TrueCrypt, Ettercap, Iceweasel, Vidalia, Wireshark, VLC Media Player, RecordMyDesktop, BleachBit, XRCed, PyCrust, aircrack-ng, Hydra, Nmap, and many others.
Features
Updated pen-testing tools Great for forensic analysis Custom hardened 3.16 kernel MATE interface with custom themes, wallpapers and icons Fast lightweight system designed also for old computers PenMode + AirMode AnonSurf functionality (tor & i2p) Pandora’s box ram cleaner at shutdown Encrypted installation Cryptocurrency friendly All the necessary for programming out of the box Cloud compatible
Rather than downloading the whole ISO, there’s also a BASH script version which turns a regular Debian Stable install into Parrot Security OS, you can find the script here: parrot-install.sh You can download Parrot Security OS here: amd64 Parrot Full – Parrot-full-1.9_amd64.iso i386 Parrot Full – Parrot-1.9_i386.iso Or read more here.